SSH KEYS AND THEIR USAGE
SSH keys are a set of security keys that ensures the safety of data in a network system. The full form of SSH keys is Security Socket Shell.
SSH keys are a set of protocols actually, which keep intruders and breaches away from the network system, thus making sure no one enters or uses the info in the network.
One can also refer to SSH keys as Security Shell.
SSH keys are actually two keys, namely public key and private key.
The idea behind introducing SSH protocol was developed after a few incidents of trespassing were seen.
The system of SSH Protocol was developed in 1995 by Tatu Ylonen.
The ideal concept behind introducing the SSH Protocol was to safeguard the servers from attackers. These attackers usually attempt to gain access through the network with the help of usernames and passwords.
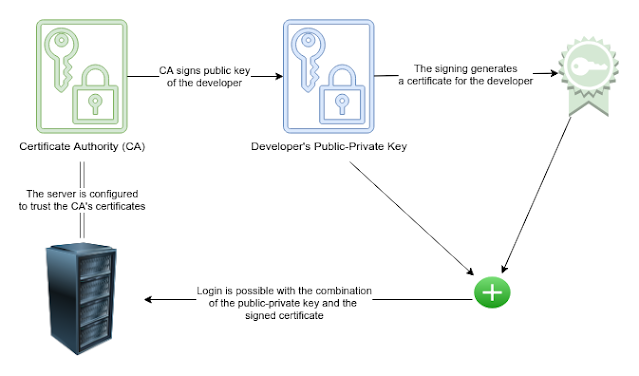
SSH keys work from two connections, the client end, and the server end. The main function/feature of SSH keys is to provide users with secure private network transactions from both ends, whether being client-side or server-side.
These keys only allow single sign-in only at one time.
The use of SSH keys is done for the following purposes -
1. Managing networks
2. Operating systems
3. Configurations.
They work by following the mechanism of the resemblance of passwords.
SSH KEYS WORKING:
SSH keys work on a client-based model and it ensures neither ends face any problem.
It usually follows a two-step process where information is shared with the client and later the access is granted after the authentication.
TIPS TO USE SSH KEYS:
Here are some tips to use SSH keys -
1. Do not enter a passphrase each time
2. Follow key management policies
3. Always keep a persistent terminal open
4. Use the agent forwarding safely and securely.


Comments
Post a Comment