BUILDING OF ZERO TRUST MODEL ARCHITECTURE

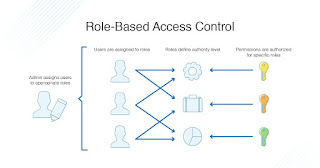
Zero Trust Model is the new buzz of the cybersecurity system. With its modern approach for providing safe network coverage, it has become the first to go choice of users nowadays. With more cases being reported of breaching happening more from internal factors, the Zero Trust Model was developed. This security system works on the principle of “trust, but verify” which means and apply as the way, your network system would trust and believe every user coming across but the access to the data and information is given once the user is providing the server with proper authentication and after they overcome the verification process. The working mechanism of the Zero Trust Model aims to safeguard data and access grants across the network by verifying the user identity and location. This security system works, inspects, and keeps track of everything, henceforth providing the network system with secured network parameters after analyzing the whole server usage and working process. Being the