RBAC (Role-Based Access Control ) and its Alternatives
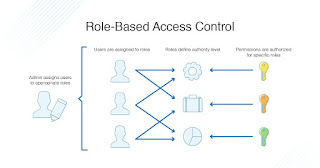
Role-based access control is the security network system that allows the grant data access to the person on the basis of their role at a specific platform. It actually means the grant access to particular information will be given to an individual as per their job profile and only that much detail would be provided to them as they need to perform their tasks.
Implementing RBAC for security, allows the higher authorities to build a tight network system for the users which henceforth makes access management easier. By following the concept of a Role-based access control system, the participant gets only limited access to the firm's data. This security level makes sure no other person intrudes on the specifics for no use and without any purpose.
There are a lot of ways by which one can perform functions to follow RBAC by the use of the custom level privilege. The custom level privilege is actually the user level mode, which somehow means that privilege to the facts and figures would be allowed only on the basis of the kind of information one requires to do their tasks. Role-based access control CLI offers two types of viewing privileges and they are -
Root view
Super view
ALTERNATIVES OF RBAC
For sure Role-Based Access Control is the most frequently adopted network security option chosen by organizations but there are a lot of other variations or one can say as alternatives of it, like ABAC and ACL.
ABAC (Attribute based control access control) - ABAC is also known as the policy-based access control system, which acts similarly to RBAC but the only difference among them is that RBAC grants access on the basis of job profile and so does ABAC too, but ABAC allow the access use specifically on the basis of a person joining time, their location and time of day.
ACL (Access control lists) - ACL aims on defining access to a person or a group of them only on the basis of the kind of document or object they need to grant permission for.
In short, one can narrow it down that ACL helps in access management from the different departments of the organization on the basis of the document.


Comments
Post a Comment