SECURITY SYSTEM WITH ACCESS CONTROL - RBAC
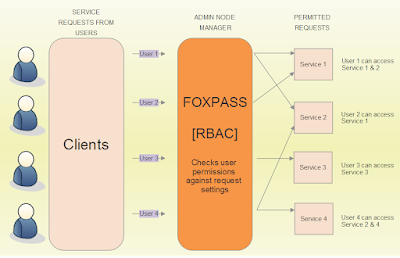
One can define role-based access control, as the method or network security system where the user is granted access to the data on the basis of the role they have at the organization they are working at. Basically, it means one can use the data of their firm, only on the basis of their job profile at the office.
RBAC, is considered one of the best network security systems for business purposes, and almost every firm uses it. The grant access granted to a particular person at the institute varies on their position and the kind of data and information, they need to perform their tasks. Just in case, if few of the employees are working on more than one project, so they’d be getting access to the data and network systems, of all the live projects they are working on and once their work is done or finished, one can remove them from the grant access list of that particular data.
It is a security system, which works on the principle of restricting system access. It specifically lays stress and follows the principle that the grant access to the data and network to a user, will be given on the basis of their working profile at the firm. It is one of the most used and well-developed yet easy security systems to use.
HOW TO IMPLEMENT RBAC?
One can easily implement, Role Based Access Control security systems for their networks. The implementation of these security systems can take place without any such chaos or mess, as it just includes some broad steps to follow.
Implementation of Role Based Access Control can be done in five simple steps, which are listed below -
1, Defining of resources and services -
2. Creating a map of roles to resources
3. Create security groups
4. Assigning users to their respective defined roles
5. Applying groups to access control lists
After the implementation is done, you can look after that no changes in the settings are made, and no user is allowed access to data, which are out of their sources.
The use of this security system is quite simple to see or to study.
BENEFITS OF USING ROLE BASED ACCESS CONTROL
One can list down the following perks of using RBAC security system :
Easily audit user privileges and correct identified issues - You can easily change and make modifications about the user’s details and can make corrections in the identifying issues as well.
Quickly add and change roles, as well as implement them across APIs - You can make quick changes about the roles of the users if there has to be some.
Integrate third-party users, by giving them pre-defined roles - The roles to the outsiders or third parties, can be granted with some access, by giving them pre-defined roles.
Reduces IT and admin load - This security system, most of all reduce to load on the IT sector, of that particular company or brand.
Reduces cost - Also, it is quite cheap to use, so it reduces the extra expense on other security systems.


Comments
Post a Comment