Role Based Access Control and its Significance.
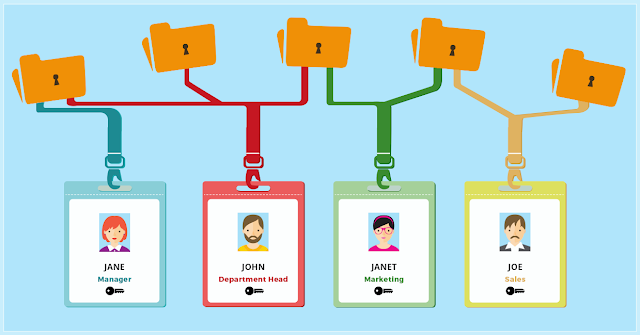
The authorization is issued in accordance with the access control policy. There are different access control policies, each one tailored to different needs. Let's see the most common Role Based Access Control RBAC. In this policy, users of the system are assigned a role that is often attached to a function in an organization. Take the example of an information system of a distribution chain, the roles are closely linked to the functional of the organization, so that we could find the roles cashier, department manager, store manager, accountant.
The security policy will define that the cashier and store manager roles have access to the opening of the cash drawer. The department manager role has access to the margins and results of his own department. And so on. Managing new and guest users can be difficult and time-consuming, but if an RBAC defines these roles before a user joins the network, the problem is resolved immediately. As soon as guests and new users join the network, their access is predefined.
Finally, it is proven that an RBAC makes significant savings for the company. An RBAC generates a significant return on investment. In the case of an imaginary financial services company with 10,000 employees, RTI estimates that the RBAC will save $ 24,000 in IT labor, and $ 300,000 in employee unavailability, each year. Automating the user access process will save you a lot more than that, just at the IT workforce level. A perfect opportunity to get a raise.
After implementation, your network will be much more secure than before and your data will be much better protected against theft. And, another advantage, the productivity of your users and your IT team will be enhanced. For us, there is no hesitation to have.
Role Based Access Control: implementation in 3 stages
What is the best way to implement role-based controls? To start on a good foundation, follow the following steps:
The good news is that you can automate this process: Foxpass lets you know who is actively using file shares on a regular basis and who is not. By assigning file access rights to roles, you will also designate a data owner for the shares. This data owner is responsible for long-term user access to the data, and can easily accept and refuse access requests made from the interface.
Once the implementation is complete, the system must remain clean. No rights that do not correspond to a user's role should be permanently assigned to them. Foxpass allows temporary access to file shares, upon request, so that the first rule is followed. However, it will be necessary to provide for a modification process allowing the roles under Role Based Access Control to be adjusted as needed.
And, of course, you need to organize regular monitoring and auditing of all of these critical resources. You should know if a user is trying to access data that does not correspond to their role, or if a right that does not conform to a user's role has been added.
The security policy will define that the cashier and store manager roles have access to the opening of the cash drawer. The department manager role has access to the margins and results of his own department. And so on. Managing new and guest users can be difficult and time-consuming, but if an RBAC defines these roles before a user joins the network, the problem is resolved immediately. As soon as guests and new users join the network, their access is predefined.
Finally, it is proven that an RBAC makes significant savings for the company. An RBAC generates a significant return on investment. In the case of an imaginary financial services company with 10,000 employees, RTI estimates that the RBAC will save $ 24,000 in IT labor, and $ 300,000 in employee unavailability, each year. Automating the user access process will save you a lot more than that, just at the IT workforce level. A perfect opportunity to get a raise.
After implementation, your network will be much more secure than before and your data will be much better protected against theft. And, another advantage, the productivity of your users and your IT team will be enhanced. For us, there is no hesitation to have.
Role Based Access Control: implementation in 3 stages
What is the best way to implement role-based controls? To start on a good foundation, follow the following steps:
- Define the resources and services you provide to your users (i.e. email, CRM, file shares, CMS, etc.)
- Create a role library: match the job descriptions to the resources defined in step 1 necessary to fulfill their mission
- Assign users to defined roles.
The good news is that you can automate this process: Foxpass lets you know who is actively using file shares on a regular basis and who is not. By assigning file access rights to roles, you will also designate a data owner for the shares. This data owner is responsible for long-term user access to the data, and can easily accept and refuse access requests made from the interface.
Once the implementation is complete, the system must remain clean. No rights that do not correspond to a user's role should be permanently assigned to them. Foxpass allows temporary access to file shares, upon request, so that the first rule is followed. However, it will be necessary to provide for a modification process allowing the roles under Role Based Access Control to be adjusted as needed.
And, of course, you need to organize regular monitoring and auditing of all of these critical resources. You should know if a user is trying to access data that does not correspond to their role, or if a right that does not conform to a user's role has been added.


Comments
Post a Comment