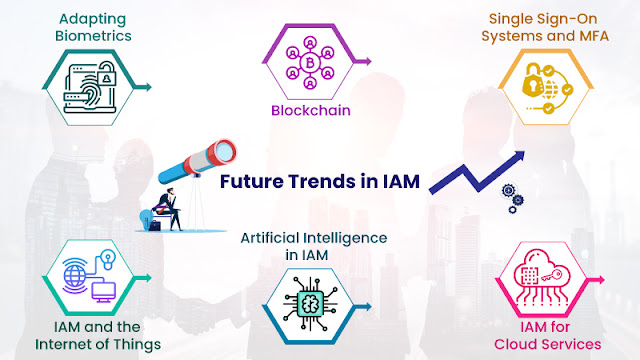
Configure Role Based Access Control
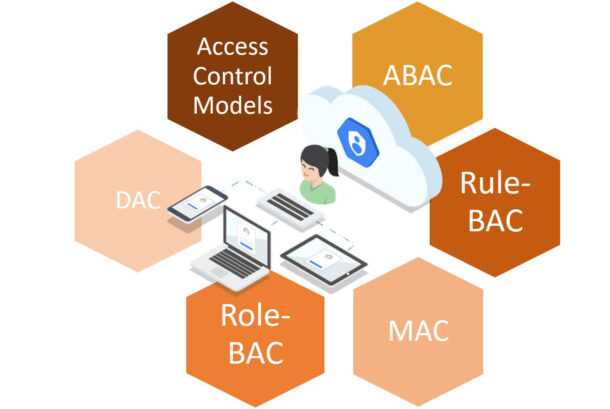
Foxpass provides role based access control (RBAC), which allows you to grant access permissions based on the roles of individual users within your organization. In Foxpass, all users are added to Foxpass Cloud. As the first user in your organization, you must first create an account in Foxpass Cloud and then log in to the Foxpass Cloud credentials. You have the super administrator role, and by default, you have full access permissions in Foxpass. Later, you can create other users in your organization in Foxpass Cloud. Users who are created later and who log in to Foxpass as regular users are called delegated administrators. These users, by default, have all permissions except user administration permissions. However, you can grant specific user administration permissions to these delegated admin users. You can do this by creating appropriate policies and assigning them to these delegated users. User administration permissions can be found in Account > User administration. For m...