A COMPLETE GUIDE - BOOK TO IAM
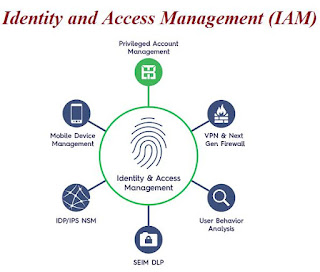
IAM stands for Identity Access Management, it is one of the core security measures used in the IT industry. The disciplined protocol of the network system works in two steps, as the name itself suggests identity and access, here in the first verification, the identity of the user is verified, thus it is confirmed that the user is the same person they are calming to be, and in the second step the user is accessed and verified on the terms of the info they can use within the network. The working mechanism of the Identity Access Management is totally dependent and is managed by the IT sector itself, also the functioning of the security system is not just limited to mankind, but with the help of smart options, its working can be made more feasible and flexible. Identity access management is a security protocol that protects the servers from both internal and external risks. Small or startup industries that are planning to make their place in the competitive market prefer to use IAM as the...
